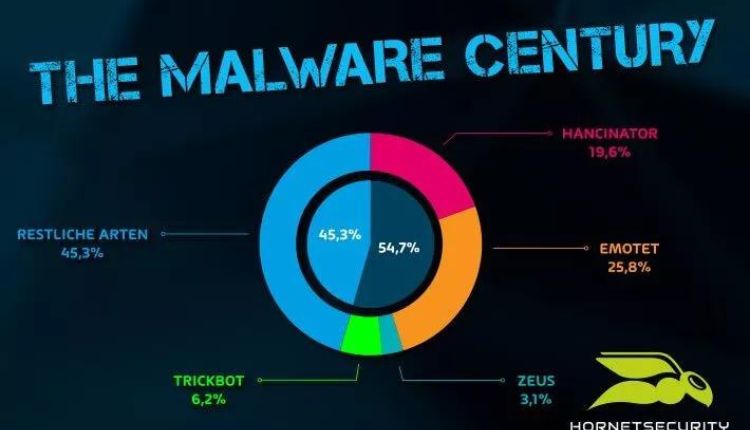
Cyber attacks have increased plenty in the last few years due to the Corona pandemic. According to antiviruses, ransomware has increased by more than 400% in the past two years. Therefore, be aware of how hackers attack and protect your sensitive information. Many hackers use multiple tools to create malware. One of these tools is malware crypter.
In short, hackers use a variety of tools such as exploits, zero-day vulnerabilities, RAT, Ransomware, Botnets, Loader, Hidden Miner, Stealer, keylogger, etc.
Each malware works in a specific way. For example, ransomware takes the sensitive information of the computer and closes the person’s access to it, and the victim has to pay the ransom. Other malware behaves differently and targets victims differently.
RAT or Remote Access Trojans make a trojan file. When the victim click on it can access all computer data hiddenly such as camera, microphone, computer drivers, etc. It is exactly as if the hacker is sitting behind your system and has access to all the details of your system.
The sealer will target your sensitive credentials and steal all accounts like bank accounts, wallet addresses, and passwords.
Botnets distribute payload to many systems. Botnets are activating on Websites such as Torrents, cracked apps, and Game patches for free. Hackers infect the game’s free patch with malware, and when the victim downloads it, their system is infected.
A hidden miner just uses your system hardware to mine the cryptocurrencies. Hackers usually use special Botnets for this to find the best computer configs. They need to best resource to mine the cryptocurrencies with victim systems.
But many of the above tools have to use Malware Crypter to bypass the antiviruses, apart from zero-day exploits and vulnerabilities.
Malware Crypter is a tool that specializes in bypassing antiviruses. Windows Defender is one of the antiviruses that is usually installed on all Windows. The malware Crypter can easily help bypass by its cryptography and obfuscation methods.
Therefore, it is most important to know how to fight against malware.
Below are the below steps to deal with this malware:
- Update all apps and software from official websites.
- Update your antivirus and enable all features.
- Never open unknown files.
- Never do updates via email.
- Do not enter or update your other accounts through the email link.
- Activate multifactor authentication (MFA) for all accounts.
- Use crypter software and encrypt your sensitive data with it. Then hackers can’t access them easily.
Note that crypter software is entirely different from malware crypter. The crypter software secures all your data based on cryptographic algorithms and limits the access of malware to it
- Use a Virtual machine for any downloading.
- Check all domains before entering & beware of Fishing.
Remember your system if infected, you should know malware crypter uses the legit system process. Note if you are a beginner and can’t find the malware.
Just search the malware on Google and ask a security professional for assistance to remove it. Many security websites guided users to restart and run the Windows safe mode. Don’t this some vulnerabilities can’t access to Windows layer & it doesn’t work.